How to Spot AI Scams and Fake Emails (2026 Guide for Pragmatic Adults)
By Rado
You open your inbox and everything looks polished. Real logos. Friendly tone. No typos. So, how do you tell what’s safe? Scammers now use AI to write perfect emails, copy real voices, and create convincing videos. In this guide, you’ll learn clear red flags that still work, a family safeword protocol for “emergency” calls, and a simple verify-before-you-pay checklist you can use every day. We’ll pull in the latest stats to show why this matters and give you steps that protect your money and your calm.
What kinds of AI scams are hitting inboxes and phones right now?
You open your email while waiting for coffee. A “bank alert” sits on top. It looks tidy, uses your name, and even references a recent purchase. A minute later, your phone rings. It’s your daughter’s voice asking for help. Feels real, right? That’s the shift: scams are no longer sloppy. AI now helps criminals write polished messages, clone voices, and even create short videos that look like the real person.
So what’s actually showing up day to day? First, AI‑written emails tailored to you. They scrape a few public details (your employer, a recent event, a board you serve on) to make the message feel familiar. That’s called spear phishing. Second, voice cloning. With just a few seconds of audio from a social post, scammers can mimic a loved one’s tone and tempo. Third, deepfake video. Short clips can place a real face on fake words. You might not see this often, but when money is involved, even a 30‑second fake can be enough.
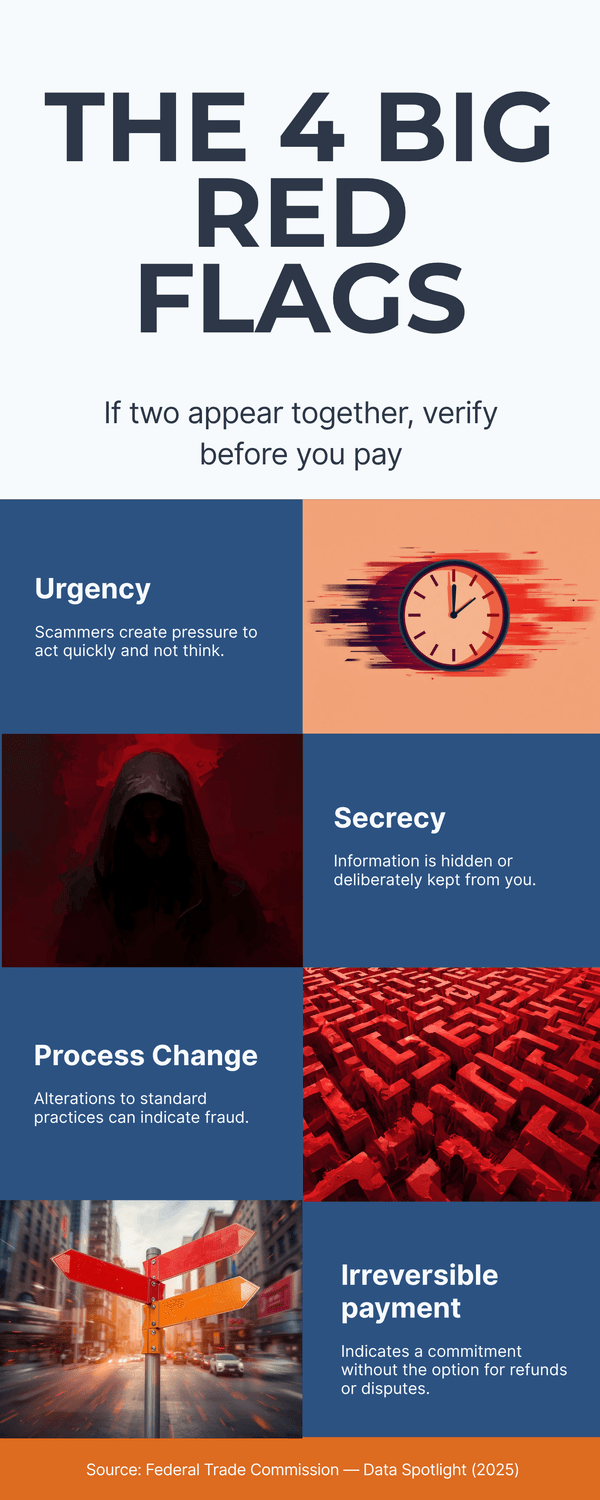
Why are more people falling for it? Because our old rule of thumb—“Look for typos”—no longer works. Modern tools fix grammar and style. The better rule is to watch for behavioral red flags: sudden urgency, secrecy, requests to break your normal process, or a push toward irreversible payments (crypto, gift cards, instant wire). Those are still solid tells.
How big is this problem? Consumer protection teams report sustained growth in losses from imposter and business‑email compromise scams, with many victims paying after a single contact (see the FTC and AARP Fraud Watch Network updates).
Industry threat reports also note rapid increases in phishing volume and quality as generative tools become easier to use (see Sift (2025)). The takeaway isn’t panic. It’s awareness: the message may look perfect, yet the request is what matters.
So, how do you respond when a very real‑looking message lands? You pause, you verify using a saved number or official app, and only then you act. That habit protects your money and your calm.
The takeaway: Expect polished scams. Don’t judge by writing quality. Judge by the request and verify it through a second, trusted channel.
How do you spot a fake email when the writing looks perfect?
You receive an email from “Accounts.” It thanks you for being a valued customer and asks you to “confirm payment” to avoid service interruption. No typos. The logo is crisp. So, what now? You switch from reading mode to verification mode.
Start with context, not commas. Does this request make sense for you today? Were you expecting a bill, refund, or password reset? Scammers thrive on surprise. If it’s out of the blue, treat it as suspicious until proven safe. You might be wondering, “But how can I tell quickly?”
Use a quick, one‑minute flow:
Ten‑second hover check: Hover over links (don’t click). Does the preview show your bank’s exact domain, or a look‑alike (small letter swap, extra word, odd country code)?
From‑line test: Expand the sender details. Many scams display a friendly name but hide a strange address. If the domain after @ isn’t the real company domain, stop.
Attachment sanity check: Were you expecting a document? If not, don’t open it. Real companies rarely send surprise ZIPs or invoice macros.
Out‑of‑band confirmation: Use a saved phone number or official app to confirm the request. Never call the number in the email.
Why does this beat AI? Because you’re validating the transaction, not the prose. Even a perfectly written fake can’t pass an independent confirmation. Security teams recommend the same habit: pause, verify on a known channel, then act (see CISA Phishing Guidance and FTC email scam tips).

Two small upgrades make this easier day to day. First, turn on two‑factor authentication for email and banking, so a stolen password isn’t the end of the story. Second, use a password manager. It will refuse to autofill on fake websites, which is a quiet but powerful tell.
It’s normal to feel unsure when everything looks real. Ask yourself: Does this match my usual process? Can I confirm it in 60 seconds through a trusted route? If yes, proceed. If not, pause.
The takeaway: Perfect writing proves nothing. Follow a simple routine—hover, check the sender, don’t open surprise files, and confirm through a saved number before you pay or share info.
What are the tell‑tale signs of AI voice scams and deepfake “emergencies”?
You’re making dinner when your phone lights up. It’s your grandson’s voice, shaky and scared: “Grandma, I need money right now. Please don’t tell mom.” Your heart races. What would you do at that moment? That sudden panic is the point. Scammers use emotion to short‑circuit your usual good judgment.
Don’t trust the voice, the number, or the urgency. Trust a process.
Common setup patterns to watch for
A loved one in trouble: car crash, hospital, jail, lost passport. The story is dramatic and time‑boxed.
Secrecy: “Don’t tell anyone” or “This has to stay between us.” That isolates you from help.
Irreversible payments: gift cards, crypto, wire transfers, courier pickups. These are hard to claw back.
“New number” script: they’ll claim their phone died and they’re on a friend’s line. Caller ID can be spoofed, so don’t rely on it.
Why voices can’t be your proof anymore
With a few seconds of audio from social media or a voicemail greeting, criminals can clone tone, pacing, even small quirks. That’s why many consumer safety groups warn that recognizing a familiar voice isn’t enough. Treat every unexpected crisis call as unverified until it passes a second‑channel check (see guidance from the FTC and AARP Fraud Watch Network).
A calm, repeatable response you can use
Pause and breathe. It’s normal to feel shaky. Give yourself 10–30 seconds; lowering stress helps you think clearly.
Hang up and call back on a saved number. Use the contact card already in your phone or an official number you trust. Do not call back the number that called you.
Ask for your family's safeword. If you don’t have one yet, set it up today: a simple word or phrase only your family knows and will never post online.
Refuse irreversible payments. If the situation is real, legitimate channels (bank card, hospital billing) will be available. Gift cards and crypto are red flags.
Confirm the location. Ask specific questions you can verify: which hospital, which police precinct, which flight number. Then independently call that place.
Extra protective habits
Tidy your public footprint. Limit public birthday videos, voicemail samples, and long talking clips that make cloning easier.
Voicemail first. Let unknown numbers go to voicemail. Scammers often avoid leaving detailed messages that could be scrutinized.
Bank alerts on. Real‑time transaction alerts give you a chance to stop damage quickly.
Report attempts. If you get one of these calls, tell your family and report at the FBI’s IC3 and your country’s consumer protection portal. More reports help patterns get shut down.
You might be wondering, “What if the call is real and I hang up?” That’s a fair question. If it’s genuine, you’ll reach your loved one or the institution by calling their known number within minutes; and you’ll avoid paying a criminal.
The takeaway: In a crisis call, verify people through a second channel before you move money. Voices can be faked; your callback routine can’t.
What simple protocols protect your family from deepfakes and cloned voices?
Imagine a Sunday afternoon. You’re sorting receipts, your partner’s making tea, and your phone pings: “Emergency—call me now.” In a world where voices and videos can be faked, you need a family protocol that works even when emotions run high.
Start with a Family Safeword
A safeword is a simple phrase only your family knows. Keep it ordinary, not a favorite quote you’ve posted online. Agree you’ll never share it in texts or emails, and you’ll only use it for real emergencies.
How to create it (3 minutes)
Choose a non‑obvious word or two‑word phrase (e.g., “map drawer” or “pepper tree”).
Write it on paper, not in a digital note that syncs everywhere.
Tell close family members in person or on a live video call you initiated.
Set a reminder to review it every six months.
When and how to use it
If someone calls with a crisis, ask for the safeword immediately.
If they don’t know it, hang up and call back using a saved contact card.
If texting, move to a second channel you already trust (e.g., phone call to a saved number or a message in an existing family chat). Don’t rely on the thread that contacted you.
Out‑of‑Band Verification (OOB)
Treat any money or data request like a locked door. You need a separate key. Use one of these:
Call back using a number you already have saved.
Ping your family group chat and ask: “Did anyone call about this?”
Confirm with a shared contact (neighbor, spouse, co‑worker) who can see the person in real life.

Crisis Payment Rules
No gift cards, crypto, or wire transfers on first contact—ever.
If payment is truly required (hospital, bail, travel), you will be able to pay through a known institution with a receipt you can verify.
Don’t pick up cash or hand it to a courier because a caller told you to.
Print‑and‑Post: One‑Page Family Scam Plan
Our safeword: _________
Callback numbers (saved in contacts):
Partner: ___________
Child 1: ___________
Child 2: ___________
Neighbor: __________
Institutions:
Bank Fraud Line: __________
Mobile Carrier Support: __________
Local Police Non‑Emergency: __________
Rules:
Pause and breathe.
Ask for a safeword.
Hang up, call back on a saved number.
Never send irreversible payments.
Keep the circle small
Share the plan with just the people who need it. The more widely it spreads, the less secret the safeword becomes.
What if someone overhears our safeword? Change it. It’s normal to rotate it, just like changing a password.
The takeaway: A safeword plus a callback routine turns fear into a checklist. It keeps your money safe and your family calm even when a voice sounds exactly right.
I’ve added this Family Safeword Protocol to my FREE AI Quick-Start Bundle so you can download, print, and protect your family today.
Grab your free copy and start building digital peace of mind.
Which tools and habits actually help without turning you into an IT pro?
You sit down with your laptop to pay a bill. Two tabs open, kettle boiling, notifications pinging. It’s easy to click fast. So, how do you stay safe without becoming your family’s tech support? The trick is to let a few simple tools do the heavy lifting and use short routines you’ll actually keep.
1) Passwords that protect you on autopilot
Use a password manager (e.g., Bitwarden, 1Password). It creates long, unique passwords and autofills only on the real site. If it refuses to fill, that’s your hint the page is fake.
Turn on two‑factor authentication (2FA) for email, banking, cloud storage. Prefer an authenticator app (e.g., Microsoft Authenticator or Authy) over text messages when possible.
2) Make your inbox do more work for you
Train your spam filter by reporting phishing, not just deleting it. This sharpens future catches.
Flag look‑alike domains with tools such as EasyDMARC’s checks or a link preview tool like CheckPhish. When in doubt, don’t click—visit the site by typing the address yourself.
Bank and card alerts: Turn on transaction and login alerts in your banking app. A 30‑second review can stop damage early.
3) Safer clicks and cleaner browsers
Keep your browser and OS updated. Set automatic updates and restart weekly. Those tiny patches close real holes.
Use built‑in protections like Safe Browsing (Chrome) or SmartScreen (Edge). They warn on known malicious pages.
Preview before you open. Hover to see the real URL or use your password manager’s saved site list as your map.

4) Phone habits that block most scams
Voicemail first for unknown numbers; real contacts will leave details you can check.
Call back on a saved number for any payment request, even if the caller ID looks right.
Silence unknown callers (iOS/Android feature) and let your contacts ring through.
5) A weekly 5‑minute safety ritual
Open your banking app: scan recent transactions and login history.
Check your email security page: confirm 2FA is on and review active sessions.
Glance at your password manager’s weak/duplicate password report. Fix one or two—small wins add up.
6) Extra credit if you want it
Set credit freezes with your national bureaus to block new‑account fraud; unfreeze briefly when you need credit.
Use Have I Been Pwned to see if your email appeared in a breach, then change those passwords.
You might be thinking, “Will this take ages?” That’s a fair question. Once set up, most of this runs quietly in the background. Your job becomes simple: pause, check alerts, and verify money moves through a trusted channel.
The takeaway: Let tools handle the heavy lifting; password manager, 2FA, browser protections, and bank alerts; then follow a short weekly check. Small habits, big protection.
How big is the problem, and why should you care now?
Picture a normal Tuesday. You’re paying a bill, booking a train, and checking a message from a friend. In the background, AI is helping criminals send more convincing emails, copy voices, and spin up fake websites in minutes. The result? More people are engaging with scams and more money is being lost.
What do the numbers say? Consumer protection agencies report billions of dollars in losses each year from imposter scams, business‑email compromise, and phishing. The volume and quality of phishing attempts keep rising as generative tools become easier to use. You can skim fresh snapshots from the FTC’s Data Spotlight and independent threat trackers like Sift to see the trend lines for yourself. The exact figures change each quarter, but the direction is clear.
So why should you care if you feel pretty good at spotting scams? Confidence can be a blind spot. When an email or call matches your routine and uses familiar details, your brain fills in the rest. That is what modern fraud leans on. Have you ever hurried through a login because you were late? Ever paid a fee on your phone while walking to a meeting? Those tiny moments are where mistakes happen.
Here’s the shift that matters: writing quality no longer separates real from fake. Many of us learned to look for typos and broken English. Today, AI fixes those tells. The reliable signs live elsewhere: urgency, secrecy, pressure to break your normal process, and requests for irreversible payments like gift cards, crypto, or instant wire. Do you see how those cues show up, no matter how polished the message is?
This isn’t about fear. It is about a calm routine that protects savings and independence. Adults 45+ are often managing family finances, helping older parents, or running small businesses. That mix of responsibility and busyness makes you a prime target. The good news is you do not need new gadgets. You need three habits you can do on a busy day:
Pause for ten seconds when money or passwords are involved.
Verify on a saved number or official app, not the channel that contacted you.
Proceed only after the request checks out.
You might be wondering, “Will this slow me down?” That is a fair question. In practice, the pause and a quick callback usually take under a minute. Compare that to the hours it takes to chase a fraudulent transfer. Which cost would you rather pay?
The takeaway: The threat level is rising, but your risk does not have to. A short pause and a second‑channel check turn slick scams into dead ends.
What should you do if you clicked or sent money by mistake?
It happens fast. You tap a link while paying a bill. Or you answer a call during a busy errand and send money to “fix” a problem. Ten minutes later, your stomach drops. If that’s you right now, take a breath. Smart people get caught. What matters is what you do next.
First 10 minutes: contain the damage
Disconnect and close. If you entered a password on a suspicious site, close the tab, disconnect Wi‑Fi, and switch your device to airplane mode.
Change passwords immediately. Start with email, bank, and any account that shares that password. Turn on two‑factor authentication.
Check recent activity. Open your banking app and email security pages. Look for new payees, transfers, or unfamiliar logins.
Call your bank’s fraud line on the number printed on your card or in the official app. Ask them to lock the account, reverse pending transfers, and monitor for new payees.
If you sent money
Bank transfer or Zelle/SEPA: Call the bank now and ask for a recall or fraud claim. Speed matters here.
Card payment: Use the app or phone number on the back of your card to dispute the charge and request a new card.
Wire or SEPA Instant: Still call. Some wires can be intercepted if you report within minutes.
Gift cards or crypto: These are hard to recover. Keep the receipts, card numbers, and wallet details. Your bank and law enforcement may still use the data.
If you clicked a link or opened an attachment
Run a full security scan with your device’s built‑in tools or trusted antivirus.
Log out of accounts on that device, then log back in after you change passwords.
Revoke access for any newly added apps or browser extensions you do not recognize.
Document and report
Write down the timeline: date, time, phone numbers, email addresses, URLs, payment method, amounts.
Report to authorities: File at the FBI Internet Crime Complaint Center (IC3) in the U.S., or your national cybercrime portal. In the EU, also notify your bank and local police.
Notify the platform: If it happened on a marketplace, social network, or email provider, report the account and message.
Check official guidance: See the FTC’s recovery steps and identity theft help for clear next moves.
Protect your identity
Enable account alerts for logins and transactions.
Set credit or fraud alerts with your national bureaus. Consider a temporary credit freeze to block new‑account fraud.
Change security questions if they use easy‑to‑guess facts. Prefer answers only you would know.
You might be wondering, “Should I tell anyone?” Yes. Tell a trusted friend or family member so you have support, and loop them in if another suspicious call comes. It’s normal to feel embarrassed. Scams are engineered to hit when you are busy or stressed. That is not a personal failing.
When to get help
You can’t access your email or bank.
New accounts appear that you did not open.
You continue getting high‑pressure calls or texts after you blocked the number.
If any of the above is true, escalate with your bank’s fraud team and local authorities. Keep your notes handy. The more detail you provide, the easier it is to act quickly.
The takeaway: Move fast, then methodically. Lock accounts, call your bank on a known number, document everything, and report. Quick, calm steps can limit losses and prevent repeat attacks.
Can AI also help you stay safe?
You’re scanning your inbox before bed. A few messages look odd, but you’re not sure why. Instead of guessing, you can let smart tools do quiet background work and keep your personal details out of risky places. Think of AI as a helpful assistant, not a decision‑maker. People verify people. Tools assist.
Where AI genuinely helps
Email filtering and link checks. Modern mail services use machine learning to spot suspicious patterns, quarantine risky attachments, and warn about look‑alike domains. Still, your best move is to type known addresses yourself or use saved bookmarks.
Anomaly alerts. Banks and payment apps use AI to flag unusual logins, new payees, or transfers outside your pattern. Turn on push alerts for transactions and sign‑ins so you can react quickly.
Identity verification. Some services add voice or face checks. Treat them as one more signal, not proof. Always pair with a second‑channel confirmation.
Browser protections. Built‑in systems like Safe Browsing or SmartScreen warn about known malicious pages. Keep your browser updated so these models have the latest data.
Privacy basics with AI tools
Do not paste sensitive data into public chatbots. Avoid account numbers, government IDs, full addresses, or one‑time codes. A simple rule from privacy groups like TrustArc is data minimization: share the least you need.
Control what’s stored. Review your account settings for any AI tool you use. Turn off training on your data when possible, and regularly delete conversation history.
Use official or enterprise modes when available. Some tools offer stricter data handling. If you do not have that option, keep sensitive tasks offline.
Follow credible guidance. Organizations such as Stanford HAI and the FTC publish practical, plain‑language tips on safe AI use.
A simple “AI‑assist” routine you can keep
Let filters work, but never rely on them alone. If money or passwords are involved, verify through a saved number or official app.
Use a password manager and 2FA. If a filtered message slips through, your accounts still have strong walls.
Check alerts, then act. When your bank flags a new payee or login, respond quickly using the app or known number.
Keep sensitive data out of chats. Ask for general advice, not account‑specific steps.
If AI gets it wrong, do I overreact? That’s a fair question. Treat alerts as prompts to double‑check, not panic. Your calm callback routine is still the final test.
The takeaway: Use AI for early warnings and smarter filters, then trust your human process: pause, verify on a known channel, and proceed only when the request checks out.
A simple routine beats sophisticated scams
You do not need new gadgets. You need a habit you can keep on a busy day. Pause for ten seconds. Verify on a saved number or in the official app. Proceed only after it checks out. That is how you protect your savings, your time, and your calm.
Ready for one action today? Get my FREE AI Quick-Start Bundle, print the Family Safeword Protocol and set a safeword. Then turn on bank alerts and two‑factor authentication. Small steps, big protection.
Frequently Asked Questions
1) What are the biggest red flags in a “perfect” email?
Urgency, secrecy, requests to break your usual process, or instructions to pay with gift cards, crypto, or instant wire. Writing quality is not a reliable signal. Use a saved number or official app to verify before acting. See guidance from the FTC.
2) How do I check if a sender is real without clicking anything?
Hover to preview links, expand the From field to inspect the full domain, and compare it to the company’s real website. If anything feels off, navigate by typing the address yourself. Tools like password managers will refuse to autofill on fake sites.
3) Can caller ID or a familiar voice be trusted?
No. Caller ID can be spoofed and voices can be cloned from short online clips. Treat emergency calls as unverified until they pass a second‑channel check. Read more from the FTC on AI voice scams.
4) What should I do in the first 10 minutes after I clicked a bad link?
Change passwords for email and banking, enable two‑factor authentication, review recent transactions and logins, and call your bank’s fraud line using the number on your card or in the official app. Then document details and file a report at the FBI IC3.
5) Are attachments always dangerous?
No, but surprise attachments are risky. If you were not expecting a file, do not open it. Confirm the request through a saved number or the company’s app first.
6) Which tools help the most with the least effort?
A password manager, two‑factor authentication, browser protections, and real‑time bank alerts. Add a weekly five‑minute check of transactions and security settings.
7) Is it safe to ask AI tools for help with security questions?
You can ask for general advice, but do not paste account numbers, one‑time codes, or personal identifiers into public chatbots. Follow a data‑minimization rule. See privacy basics from TrustArc and Stanford HAI.
8) Should I freeze my credit?
A credit freeze helps block new‑account fraud. It is free in many countries and you can temporarily unfreeze when needed. Pair it with transaction alerts and strong passwords.
9) If I run a small business, what extra steps matter?
Use custom domains with SPF/DKIM/DMARC, enforce 2FA for staff, require out‑of‑band approval for any payment change, and train a one‑minute verification routine. Check DMARC and domain health with tools like EasyDMARC.
Sources:
Federal Trade Commission — How to Recognize and Avoid Phishing Scams (2025).
Federal Trade Commission — Data Spotlight (2025).
FBI — Internet Crime Complaint Center (IC3) (2025).
CISA — Phishing Guidance, Stop.Think.Connect. Toolkit (2025).
AARP — Fraud Watch Network (2025).
Sift — Resources and Fraud Intelligence Reports (2025).
TrustArc — Privacy Resources (2025).
Stanford HAI — Publications and Guidance (2025).
McAfee — AI Voice Clone Scams: What to Know (2024).
EasyDMARC — Email Security Tools (2025).
CheckPhish — URL and Website Risk Checks (2025).

